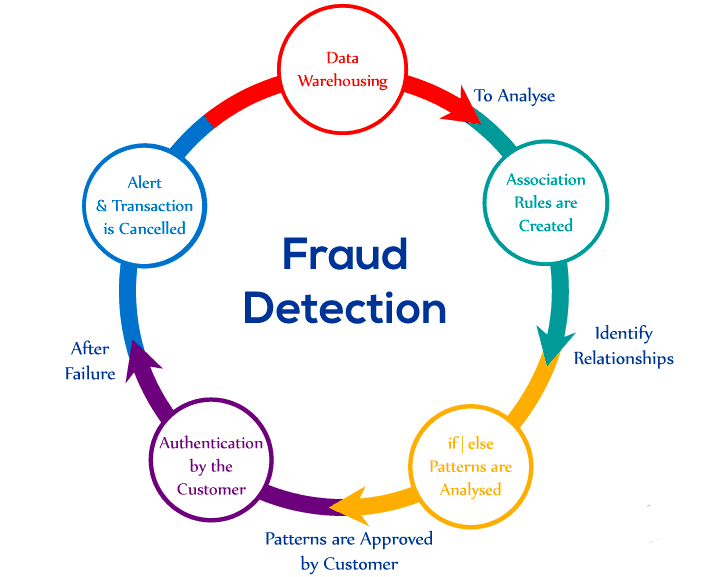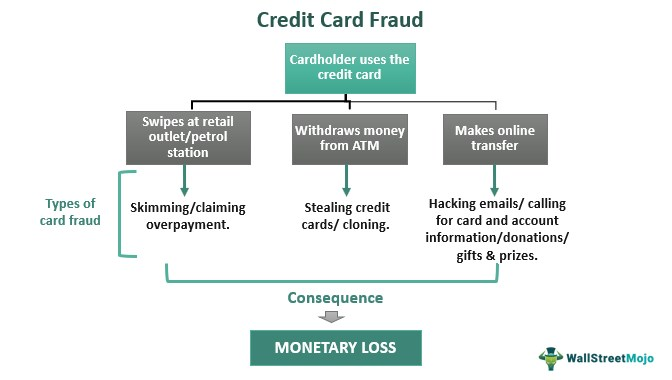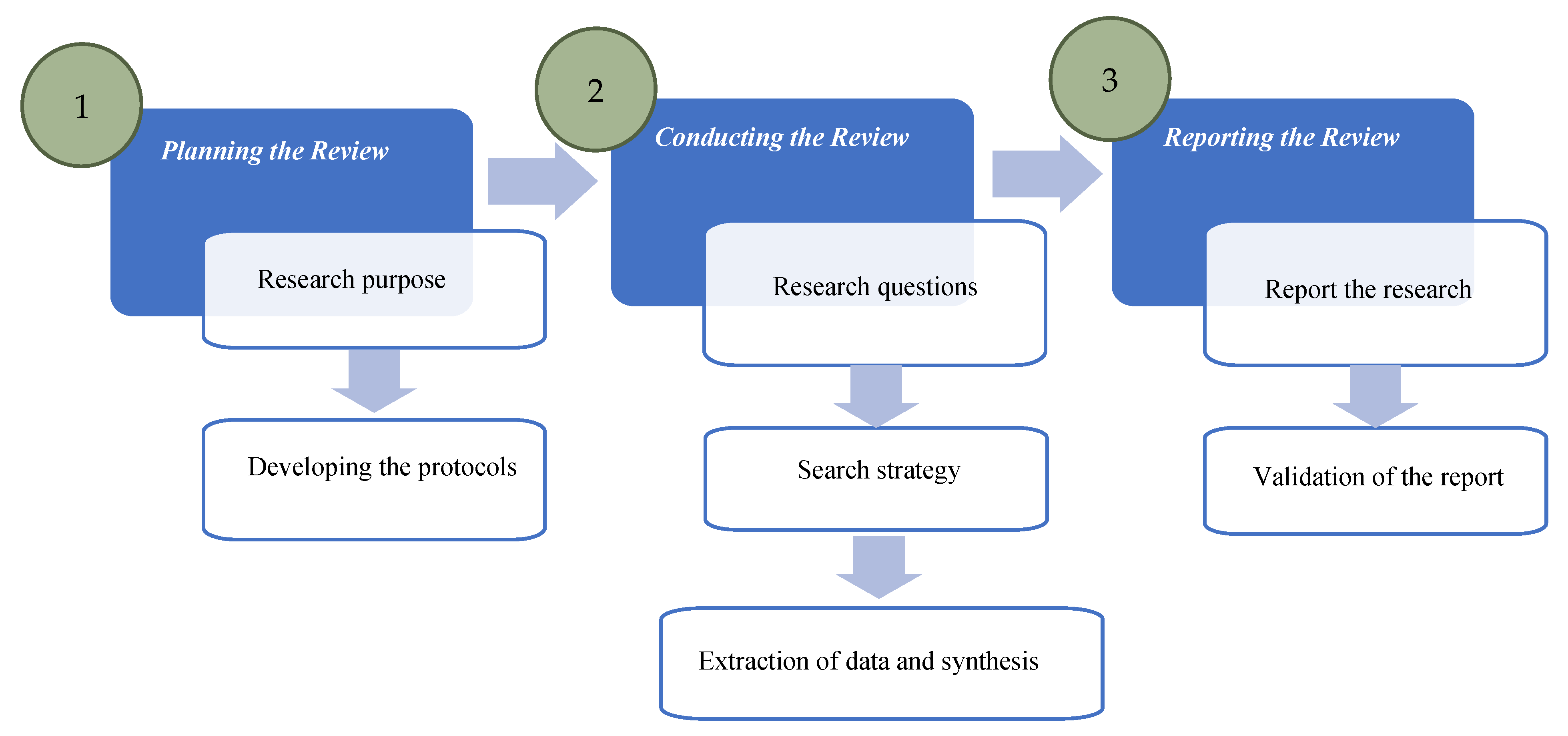
Applied Sciences | Free Full-Text | Financial Fraud Detection Based on Machine Learning: A Systematic Literature Review
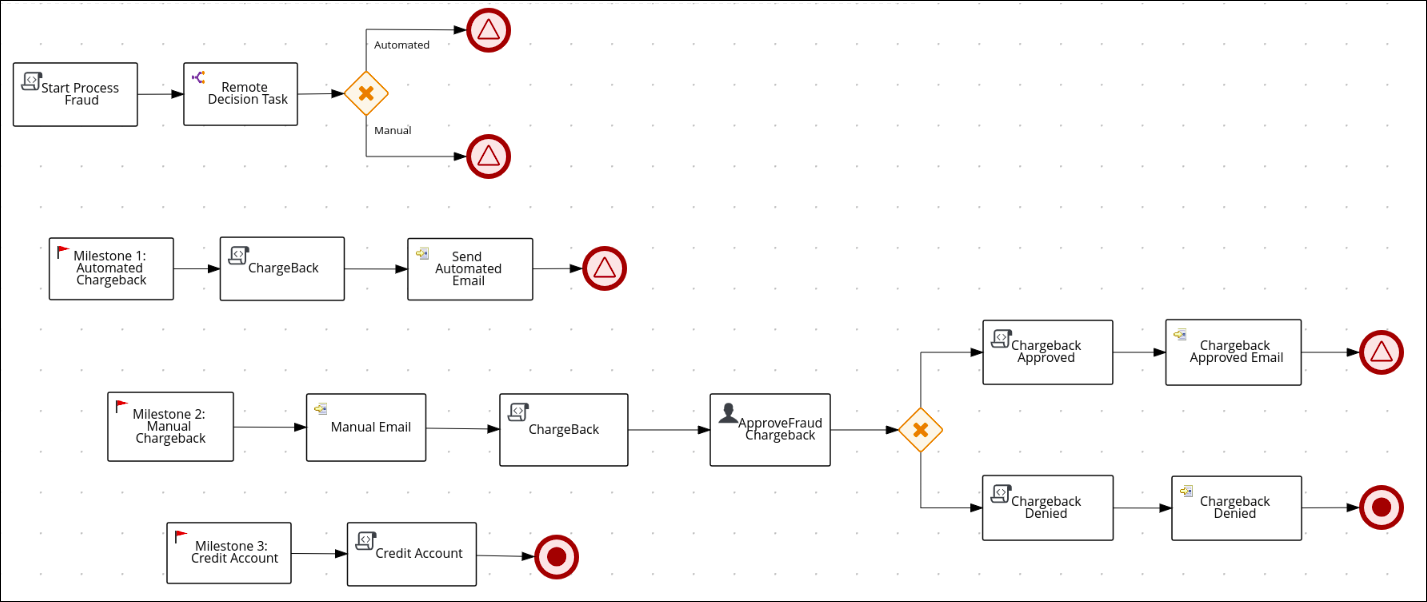
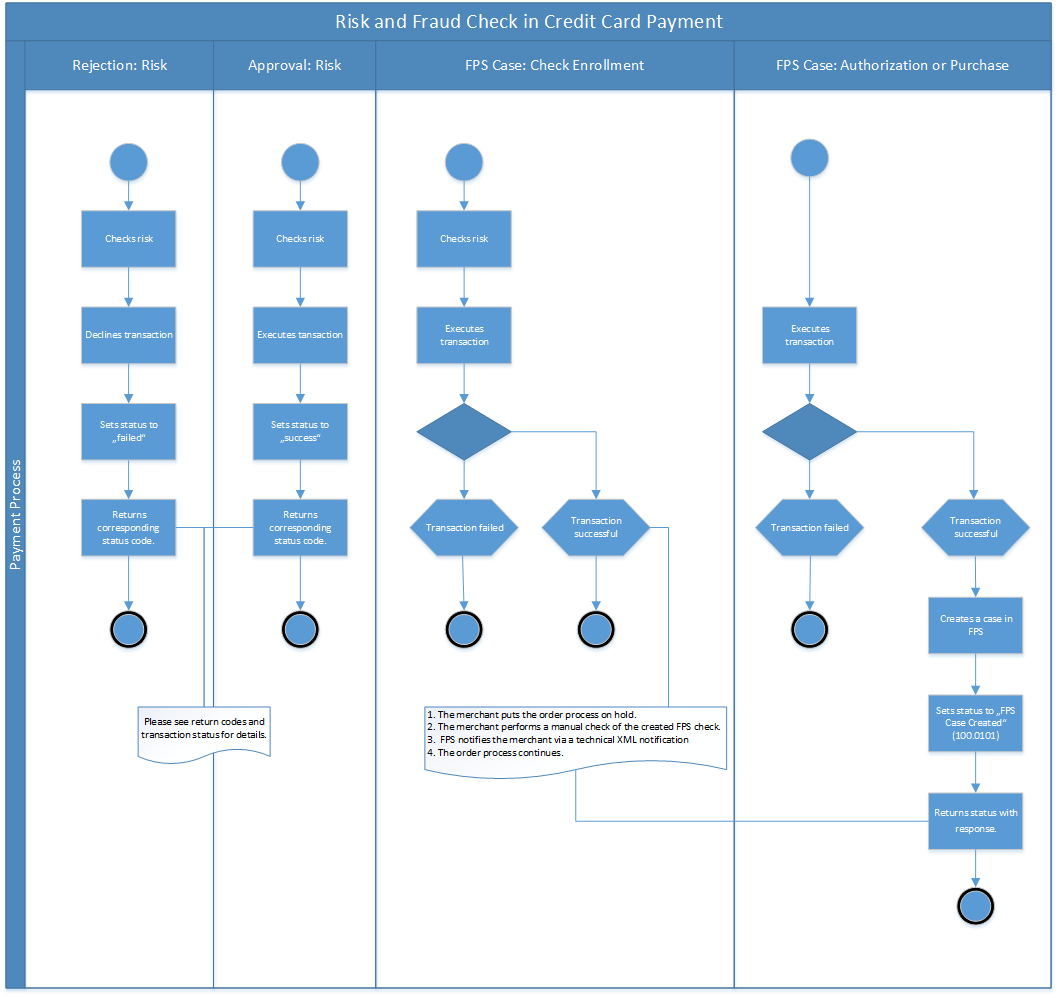
Chapter 91. Credit card fraud dispute use case Red Hat Process Automation Manager 7.10 | Red Hat Customer Portal

Computer forensics in IT audit and credit card fraud investigation - for USB devices | Semantic Scholar

Exploratory analysis of credit card fraud detection using machine learning techniques - ScienceDirect
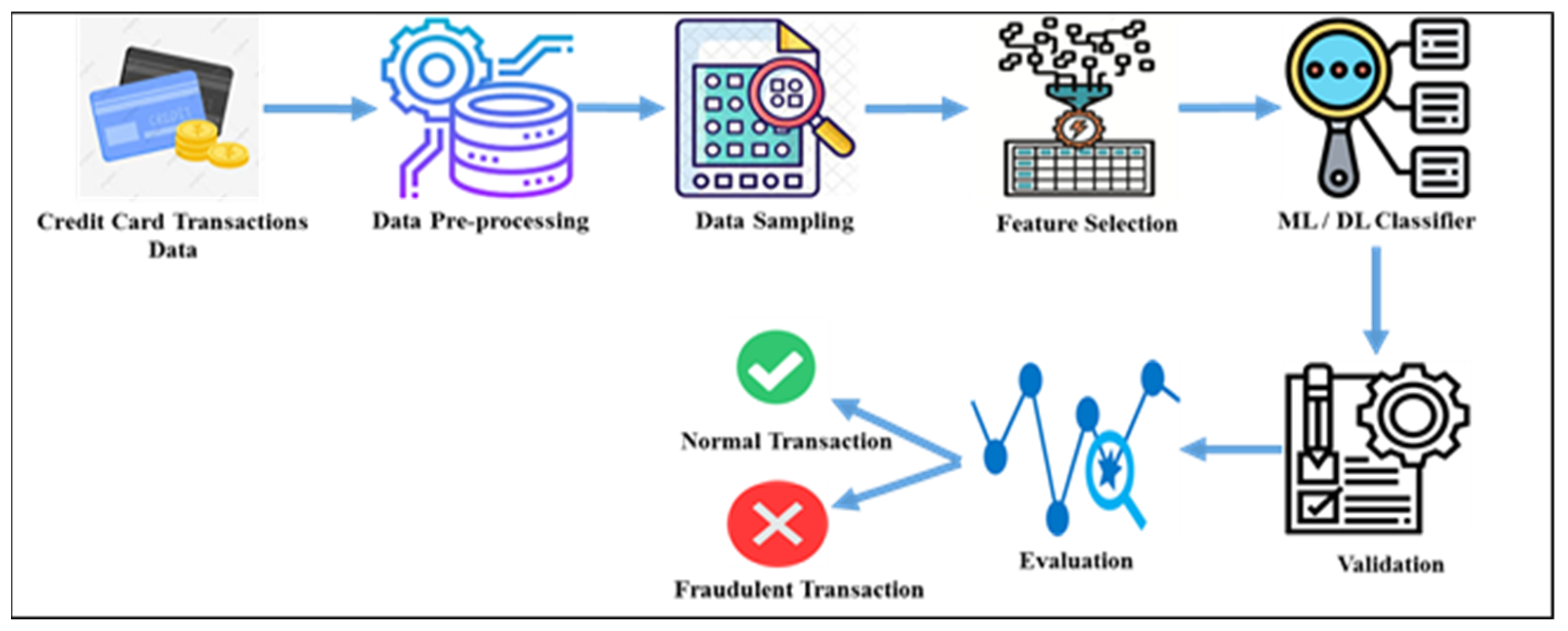
Electronics | Free Full-Text | Survey of Credit Card Anomaly and Fraud Detection Using Sampling Techniques

Example of an uncertain case from the credit card fraud investigation... | Download Scientific Diagram
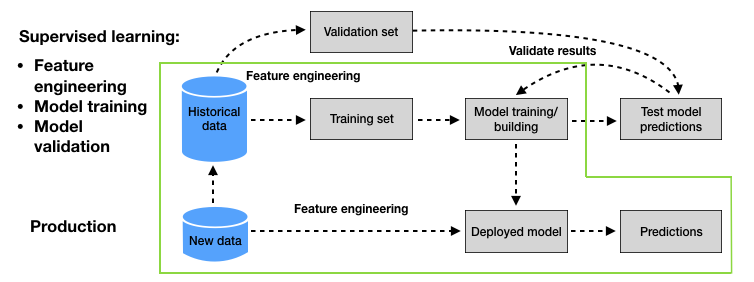
4. Baseline fraud detection system — Reproducible Machine Learning for Credit Card Fraud detection - Practical handbook