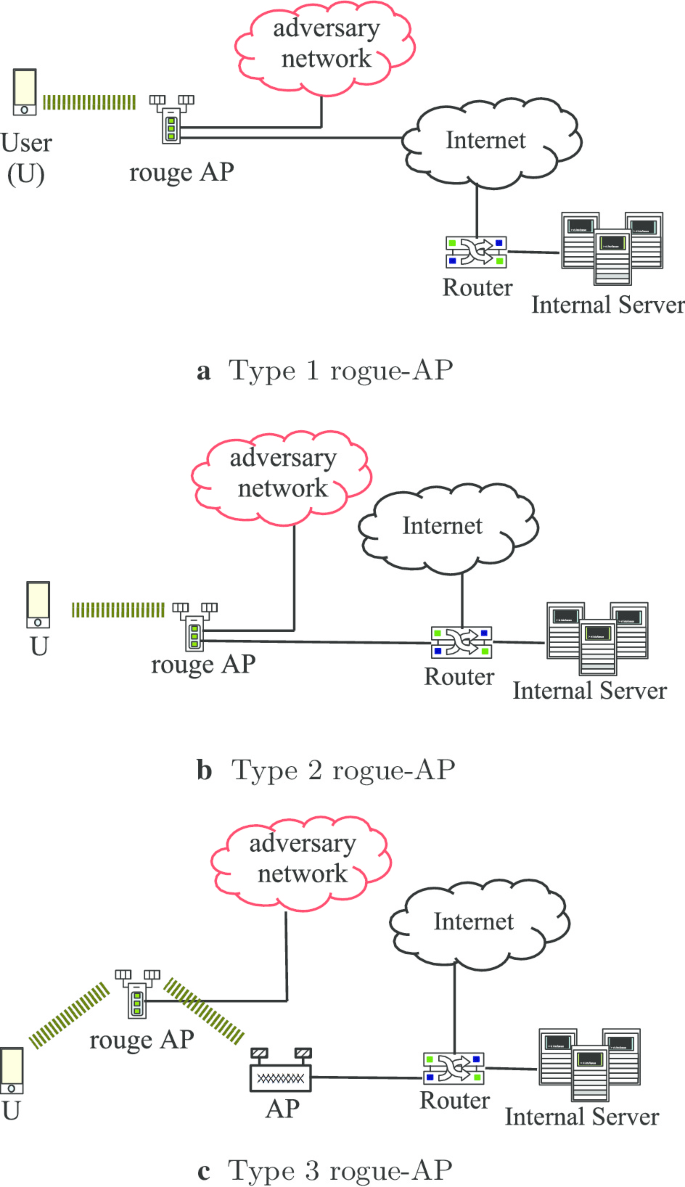
PRAPD: A novel received signal strength–based approach for practical rogue access point detection - Wenjia Wu, Xiaolin Gu, Kai Dong, Xiaomin Shi, Ming Yang, 2018

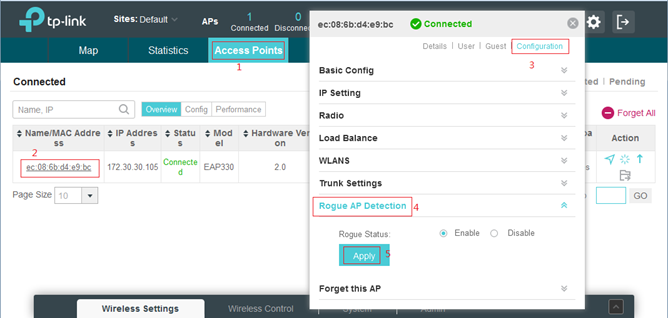
Linksys Official Support - How to enable Rogue AP Detection on your Linksys Wireless-AC Access Point
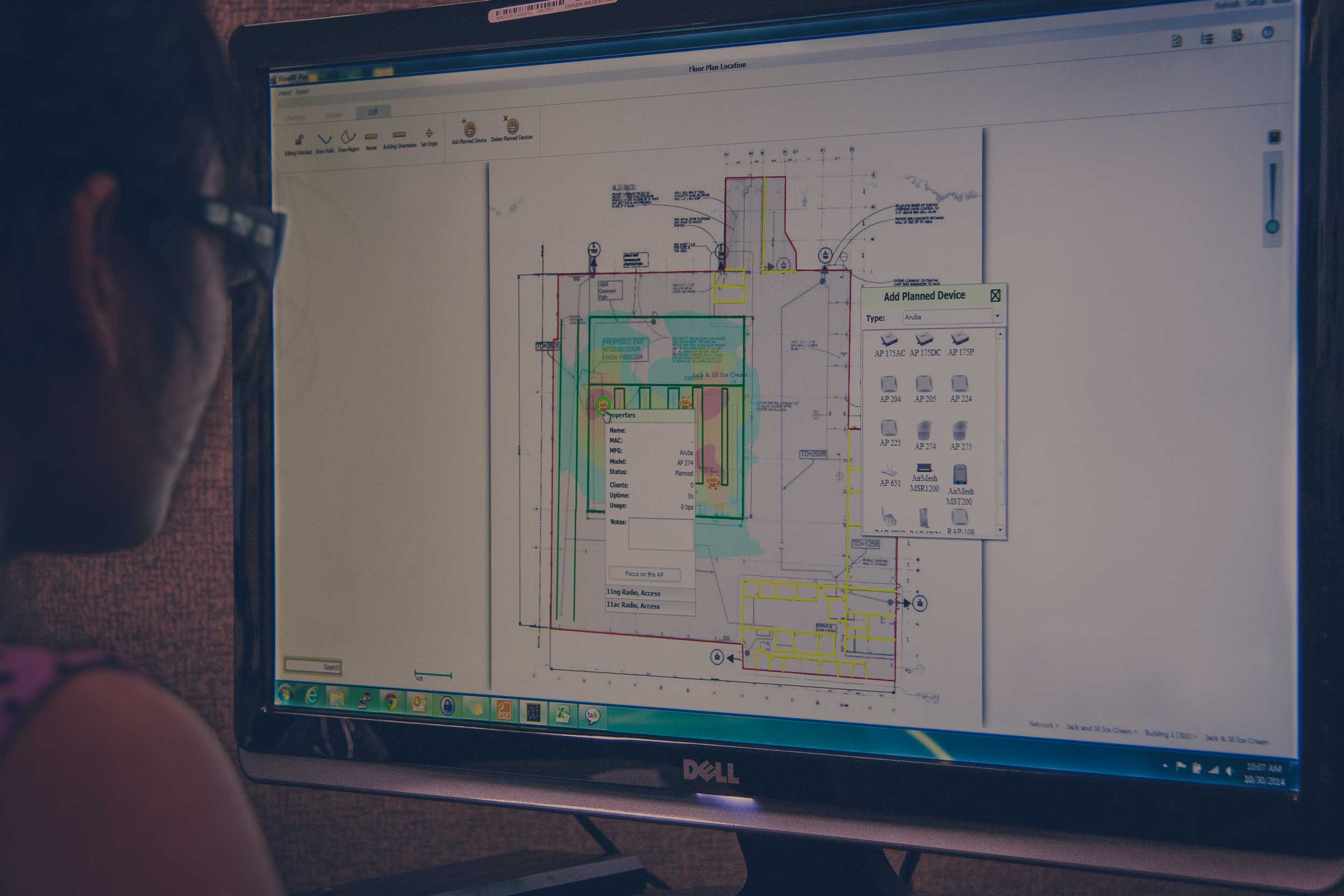
GitHub - naren-jayram/CiscoPrime-Rogue-AP-Detection: Automation of the process to detect rogue access points by identifying all the foreign access points (*AP that does not belongs to organization's wireless network Infrastructure*) that resides in
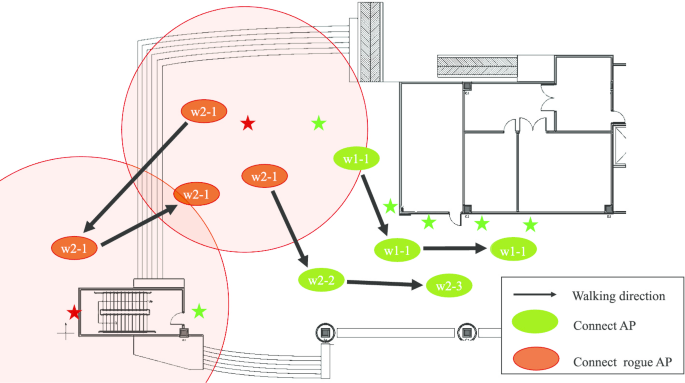
Client-side rogue access-point detection using a simple walking strategy and round-trip time analysis | EURASIP Journal on Wireless Communications and Networking | Full Text




![PDF] A Timing-Based Scheme for Rogue AP Detection | Semantic Scholar PDF] A Timing-Based Scheme for Rogue AP Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/513b85e71d91eb6e490646519537ce2b50f36c2a/3-Figure2-1.png)




![PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar PDF] A Flexible Framework for Rogue Access Point Detection | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5f7a2fec5198aa5b1f3c846b4db50aec4dff4e3b/29-Figure2.2-1.png)